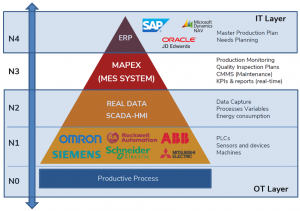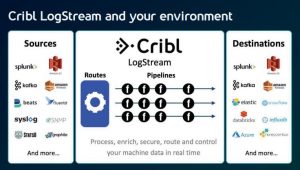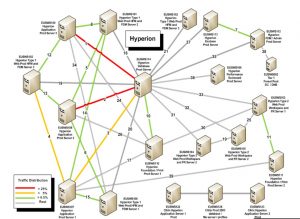
Application Discovery and Dependency Mapping
Application Discovery and Dependency Mapping (ADDM) discovers applications running on servers and network devices within the network infrastructure, and maps the dependencies between them. It aids in discovering, mapping, and is critical when considering Cloud migration.