Book now and get 15% off all Services
SERVICES

Application Performance Management
It is fundamental understanding of applications and how they are work when understanding the performance and when things go wrong, why and how to fix it.
As a part of our services, we are able work with unique technology that helps us to understand the way that the application communicates with the network and how this interaction across a LAN and WAN can result in poor performance.
We can profile this behaviour to give you an accurate architecture and Help to map you critical applications and the understand the application dependencies. Ensure that the infrastructure is optimized and the application is performing optimally and without excess expense and infrastructure. This starts with a free Health Check workshop. To find out more hit the link to see ICT Analytics or if you would like to try a free Applicayion Audit then hit that link.
Network Device Discovery
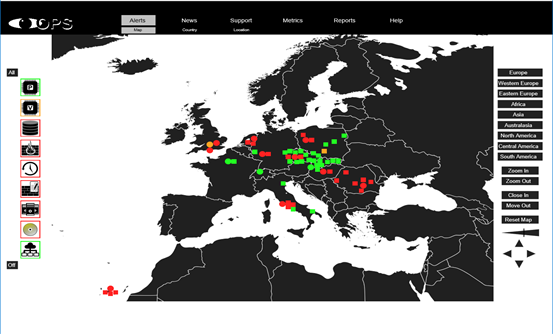
We can provide an extensive report on your networks, auto discovering devices, firewalls, load balancers and other network devices. We can run a detailed report on end-user activity and configuration data. The Full Network Assessment Report includes every detail, presented in line-item fashio. This can focus on specific areas of interes, problem areas are highlighted in red.
We can give you a risk score against peer networks and areas to work on. This audit can be used weekly or monthly to demonstrate the progress you are making towards a better risk score.
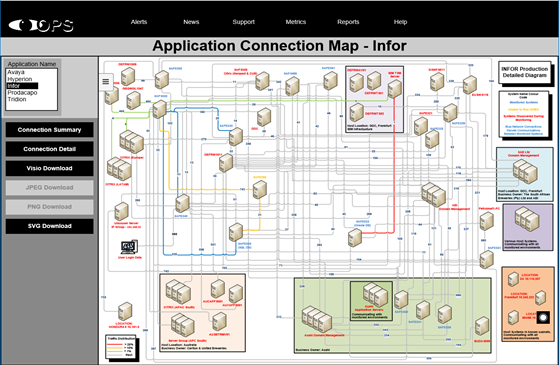
Application Dependency Mapping
Application Dependency Mapping is aimed at identifying the devices, interconnectivity and information flows that form the basis of a deployed application in an ICT infrastructure. Once the data has been captured and uploaded, production of the maps is a semi-autonomous process. In a complex application environment, application maps are key to troubleshooting, migration, or decommissioning.
Features include:
* Discover infrastructure dependencies and data-flows for an application
* Visualize an Application Map
* Assists the planning of migrations to new infrastructures or cloud
* Uncover unknown dependencies
* Critical for investigating faults and trouble tickets
GDPR Data Discovery
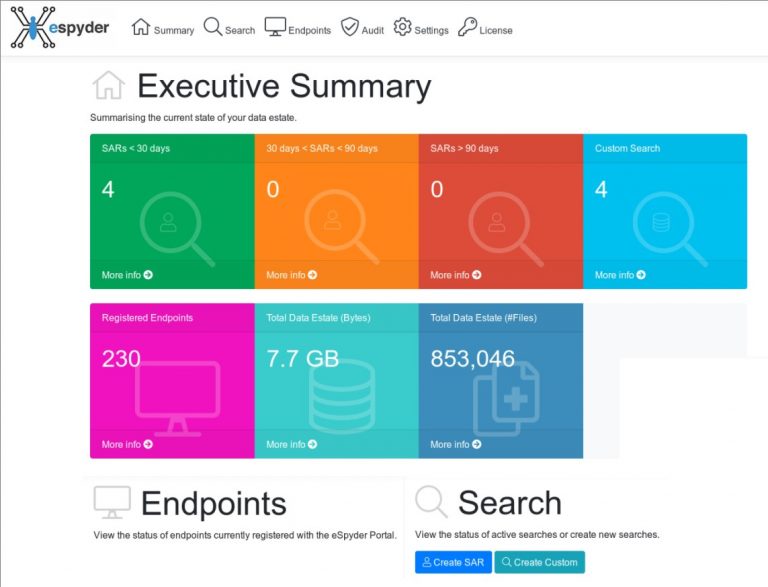
GDPR Data Discovery has been designed from the ground up to support Data Processing Officers (DPOs) in their roles, safeguarding your Personal Identifiable Information (PII) & intellectual property and making sure of compliance with the GDPR regulations and best business practice.
Data Discovery allows DPOs to respond to Data Subject Access Requests (SARs) easily and quickly. It also allows you to track your progress in terms of SARs processing and corporate data storage and retention.
Designed to be invisible and seamless for users on one hand, but fully configurable for administrators on the other hand. While supporting efficient, highly flexible Search & Indexing configuration and deployment options, it easily blends into existing IT environments
without the need for additional server infrastructure.
Vulnerability Scanning
In today’s hostile cyber world, regular vulnerability scanning has become a “must-have/must do” extra layer of cyber security protection for every network you manage. The National Institute of Standards and Technology recommends that vulnerability scans be run at least quarterly, regardless of network size or type. However, for any organization that relies on continuous availability of their computer network for regular operations, you should run a vulnerability scan monthly . . . and even more frequently for organizations that collect and/or process personal or sensitive data.
The slick dashboard functionality allows you to review the health and status of every device you manage. Issues can be sorted by device, type or severity. Drill down into impacts, solutions and insights needed for remediation. Access your Vulnerability Scanner portal from anywhere on any device at any time.
IT Security Assessment
- Collects detailed information on every asset, including those not physically connected to the network.
- Identifies all risks from misconfigurations, network vulnerabilities and user threats.
- Supports all environments, from on-premise, to remote, to cloud, to work-from-home.
- Complete Data with No agents for a fast yet full picture.
- Recurring assessments to adapt instantly to change for all clients.
- Instant reports and remediation plans fully-branded and ready to present.
- Affordable monthly service.


SIEM Dashboard with Sumo Logic
A central console to track and monitor all your Applications, Servers, Network and Security devices.
Cloud SIEM Managed Service
Quickly detect application and security incidents
Faster troubleshooting with integrated logs, metrics and traces.
