Sumo Logic Cloud SIEM
A Security Incident Event Management (SIEM) solution is used to analyze security event data in real time to achieve early detection of attacks and breaches.
Once an incident is identified the SIEM should allow investigation, remediation and reporting of the incident for both policy and regulatory compliance.
A SIEM is generally driven by log data ingested from security devices, network infrastructure, host and endpoint systems, applications, and cloud services. Additional data, such as network packets, may also be used.
The SIEM will then provide a UI for network security event monitoring, user activity monitoring and compliance reporting. This will happen in near real time, such that incidents may be responded to as soon as they are detected. In addition, the SIEM will provide for historical analysis such that trends and management reporting may be reported.
The National Institute of Standards and Technology (NIST) categorize attack vectors in the following categories:
• External/Removable Media: An attack executed from removable media (e.g., flash drive, CD) or a peripheral device.
• Email: An attack executed via an email message or attachment (e.g. malware infection).
• Attrition: An attack that employs brute force methods to compromise, degrade, or destroy systems, networks, or services.
• Improper Usage: Any incident resulting from violation of an organization’s acceptable usage policies by an authorized user, excluding the above categories.
• Web: An attack executed from a website or a web–based application (e.g. drive–by download).
• Loss or Theft of Equipment: The loss or theft of a computing device or media used by the organization, such as a laptop or smartphone.
• Other: An attack that does not fit into any of the other categories.
A SIEM should therefore:
• Enable these attack vectors to be monitored
• Effectively categorize threats to minimize operator fatigue
• Operate at scale and at reasonable cost. Security logs can be very voluminous, so a
SIEM that licences purely on a per GB ingest model can become very expensive
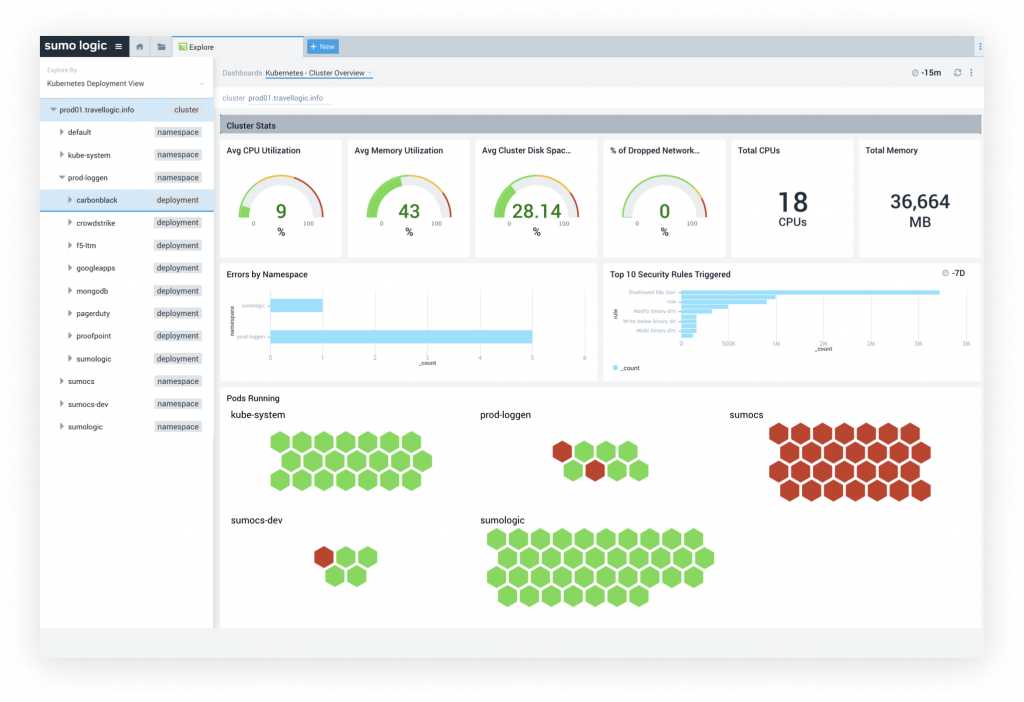
Cloud SIEM Enterprise provides a convergence of data sources, collecting millions of logs and security–relevant data from cloud, on–premises, and hybrid architectures.
Pattern and threat intelligence matching with correlation logic, statistical evaluation, and anomaly detection filter the raw records down to thousands of Signals in near real–time.
Insights represent the intelligent, correlated, and prioritized clustering of Signals to reduce the analyst workload down to 10’s of incidents for investigation. Insights dramatically decrease validation and investigation times by presenting an automatically generated
storyline of potential security incidents containing all the relevant context analysts require to make rapid response decisions.
Insights are generated by the Adaptive Signal Clustering (ASC) engine using principles modeled on the actions of world–class SOC analysts to group related Signals worthy of human review. This provides analysts with the identification and context of an attack and its movements, including multiple low–severity Signals that often fly below the radar.
ASC engine algorithms are continuously improved as customers identify patterns, validate Signals and Insights, or add new searches—thereby increasing confidence levels and benefiting all Sumo Logic Cloud SIEM Enterprise users.
Sumo Logic Cloud SIEM Enterprise includes collectors beyond just logs. The open–source Zeek network security monitor performs deep packet inspection and reassembles network traffic flows into rich protocol–level network sessions, extracted files, and security context.
Using the Cloud SIEM Enterprise console, analysts can see raw network traffic details, related connections and protocol activity, and gain visibility into East/West network traffic.
Cloud SIEM Enterprise collects asset information for users and devices—including info natively from Active Directory—to deliver additional context like anomalous activities by users and devices.
Cloud SIEM Enterprise’s deep library of native cloud API integrations can pull security telemetry directly from sources (e.g., Carbon Black, Okta, AWS GuardDuty, Office 365) simply using an API key.
In summary, the Sumo Logic Cloud SIEM Enterprise solution provides:
• A cloud native SIEM with no on–prem infrastructure costs
• An innovative pricing model that can offer substantial savings over leading SIEM
solutions
• A full feature capability to support in depth incident analysis and reporting
• An open API, for integration with other services
